Privacy and Security Challenges in Integrated Sensing and Communications
NYU Wireless P.I.s
Research Overview
Integrated sensing and communication (ISAC) has emerged as a key enabler for next-generation wireless networks. However, combining sensing and communication within a single platform also introduces new privacy challenges for both the transmitter and the sensing targets. While the privacy risk to the transmitter resembles that of conventional communication systems, the presence of sensing constraints makes optimization problems fundamentally different. In contrast, the privacy risk to sensing targets is entirely new in ISAC. Alongside privacy, the problem of secure ISAC arises when trying to sense an environment via sensing and communication signals, which opens a challenge of leaking communication data, which must be addressed. We need to deal with security concerns as communication waveforms containing information are now being utilized to detect targets.
In this project, we develop optimization-based solutions for physical layer security and privacy preservation in ISAC systems.
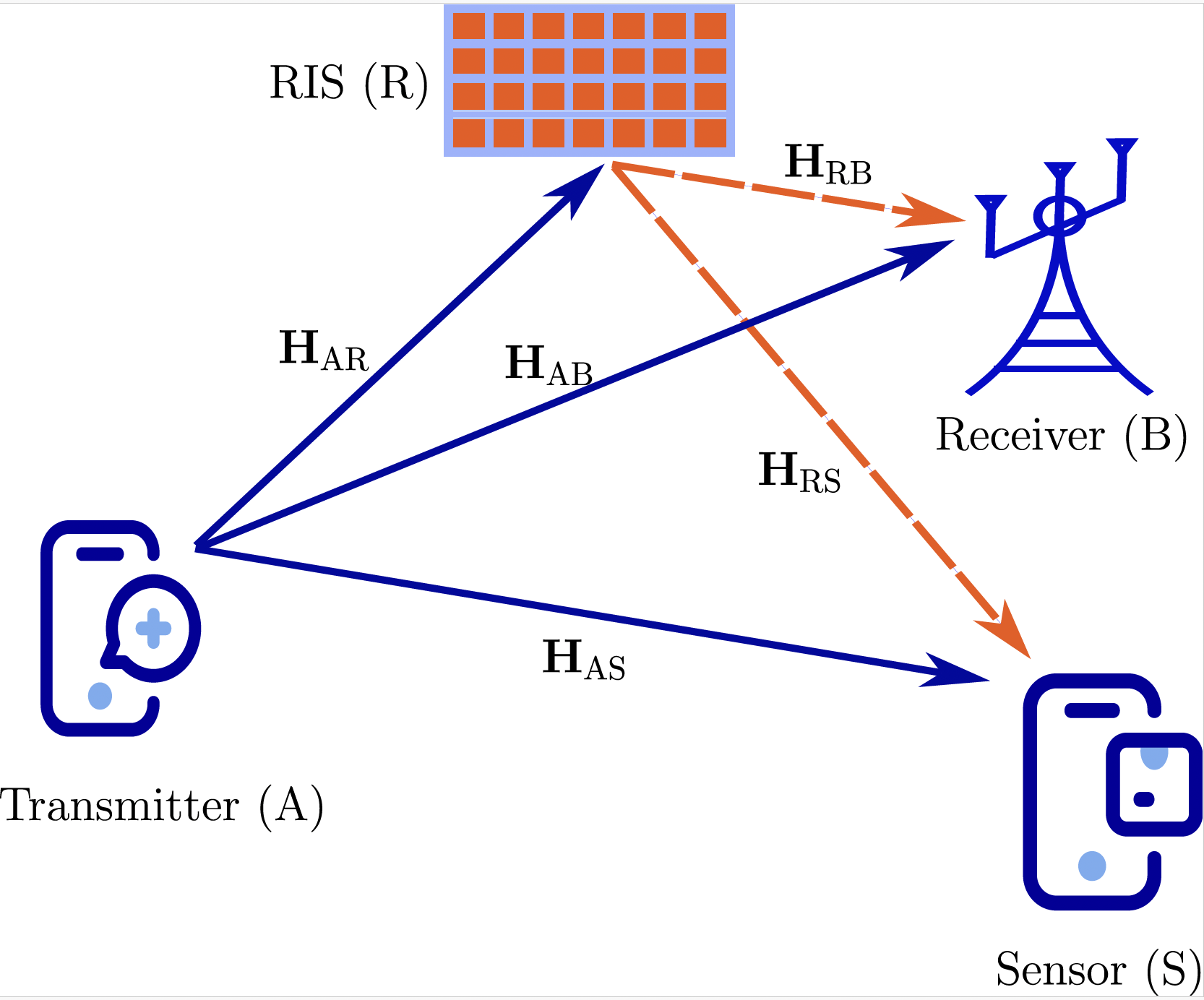
- In our first study, we focus on the transmitter privacy. A transmitter should be able to communicate without being sensed. Our study prevents a malicious sensor from reliably estimating the transmitter–sensor channel by leveraging a reconfigurable intelligent surface (RIS). We jointly design the transmit waveform and RIS configuration to guarantee a minimum communication quality-of-service (QoS) while maximizing the channel estimation error at the sensor, under a transmit power budget.
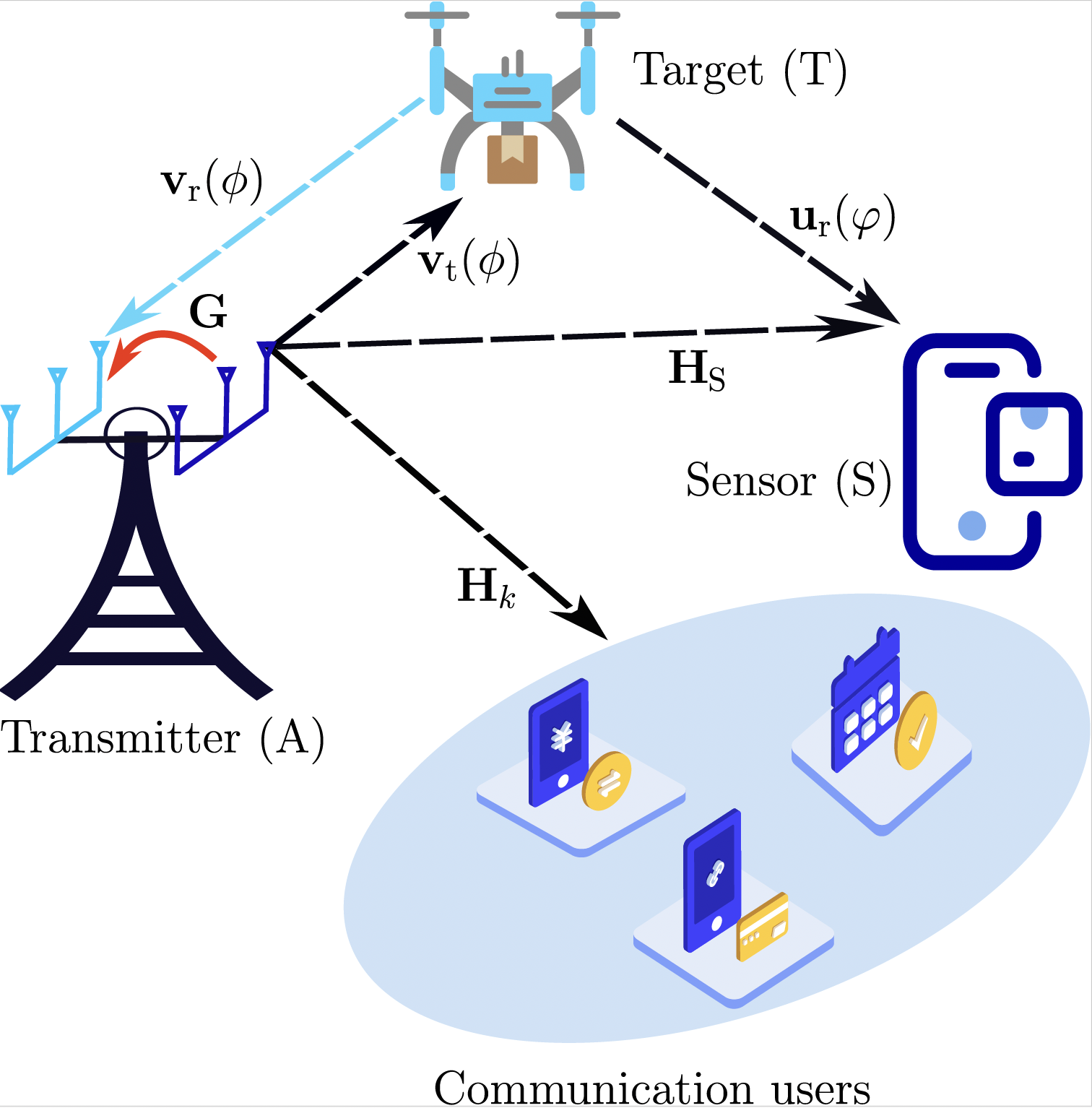
- In our second study, we address the target privacy. When the base station illuminates a target, we want to ensure that a malicious sensor cannot reliably detect the presence or absence of a target.
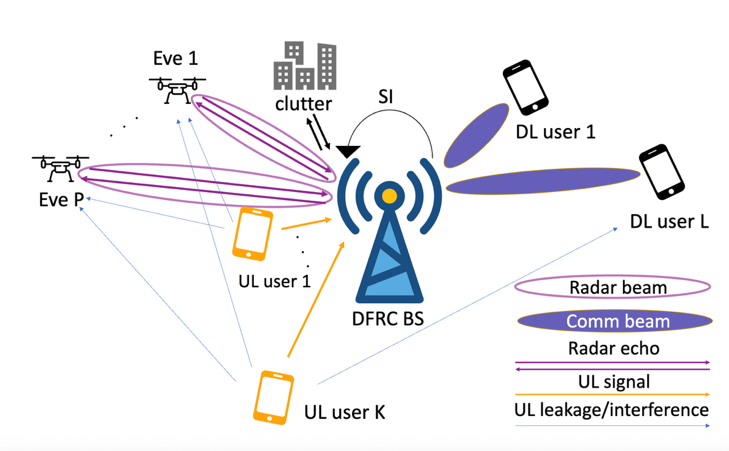
- In our third study, the communication signal is used for sensing and we want to prevent the target from decoding communication information. For that, we assess the secrecy rate achievabilities under minimal power consumption. We model a secure ISAC system, in different modes, such as half-duplex and full-duplex ISAC.
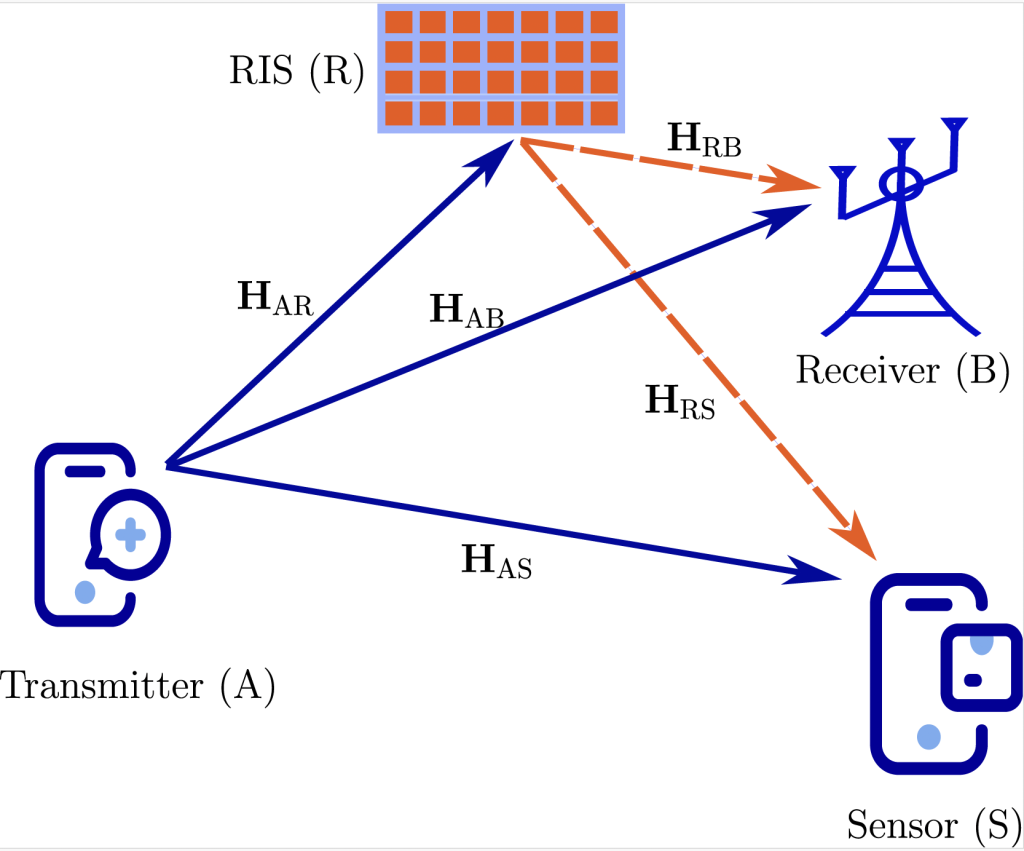
Fig. 1: System model for transmitter privacy in ISAC.
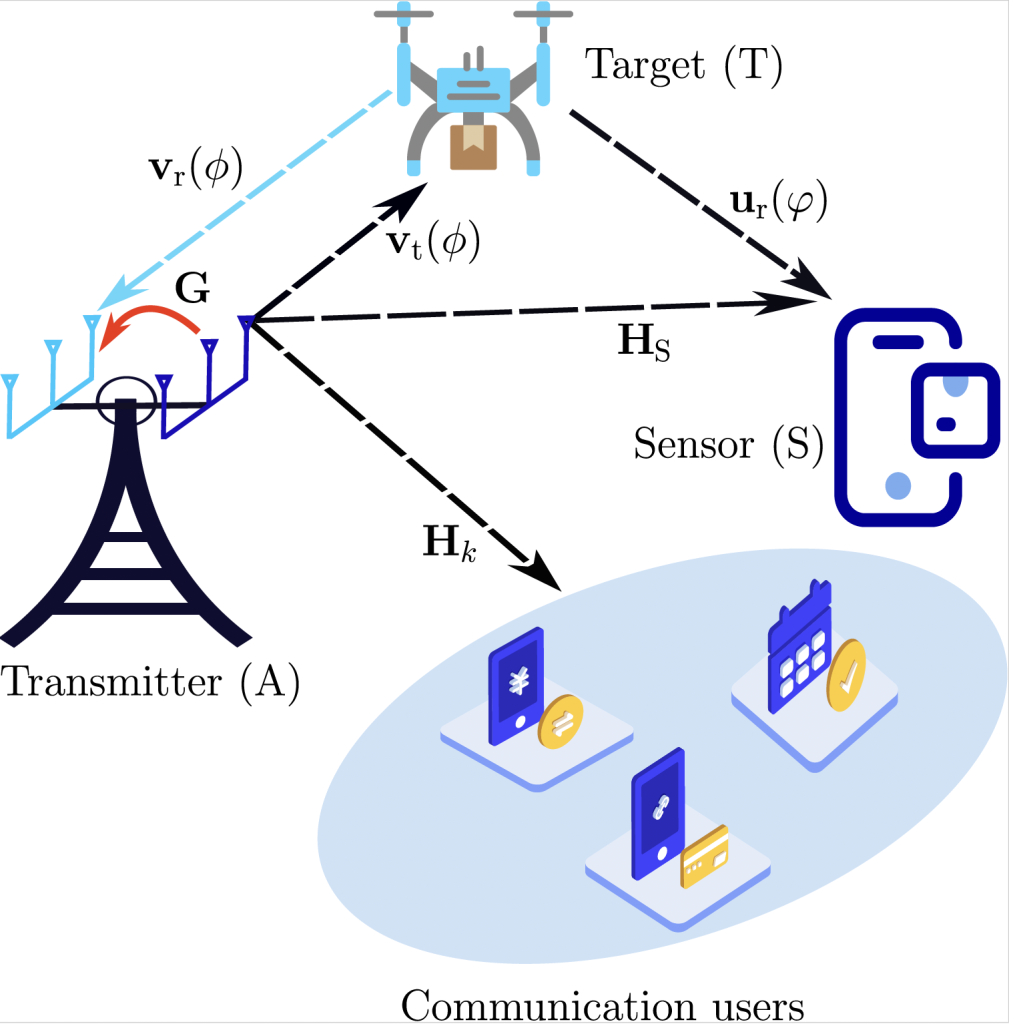
Fig. 2: System model for target privacy in ISAC.

Fig. 3: System model for secure ISAC.

 2026 Open House
2026 Open House 2025 Brooklyn 6G Summit — November 5-7
2025 Brooklyn 6G Summit — November 5-7 Sundeep Rangan & Team Receive NTIA Award
Sundeep Rangan & Team Receive NTIA Award