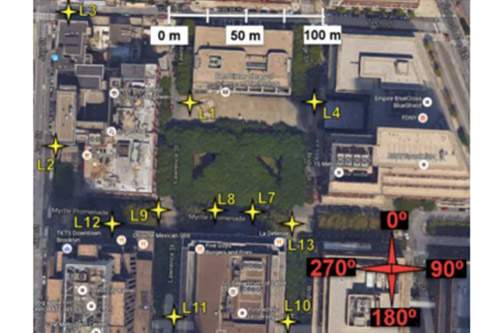
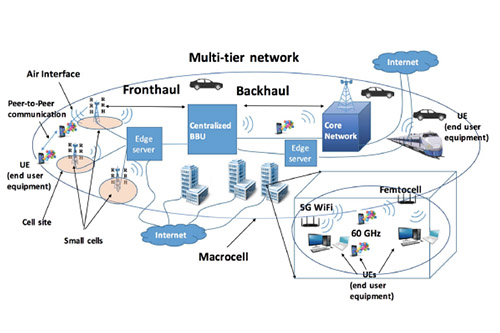
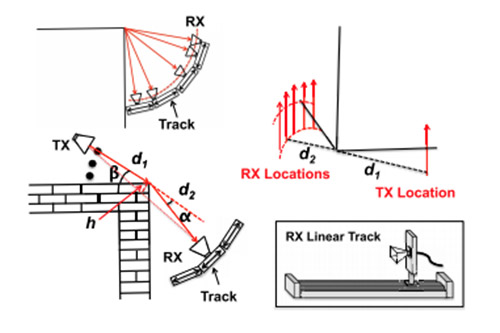
Covert Communications of Hardware Trojans
NYU Wireless P.I.s
Research Overview
The primary objective of covert communication is to conceal the transmission of signals within the inherent randomness of the wireless channel such as receiver noise, fading so that the presence of communication cannot be detected by a warden. Prior research has shown that, asymptotically, the covert capacity approaches zero. Subsequent studies have demonstrated that introducing additional sources of uncertainty, such as the warden’s lack of channel state information, can enable a positive covert capacity. Our work considers a practical wireless communication setting where a hardware Trojans embedded in a legitimate receiver tries to communicate covertly to its intended receiver (see Fig. 2).
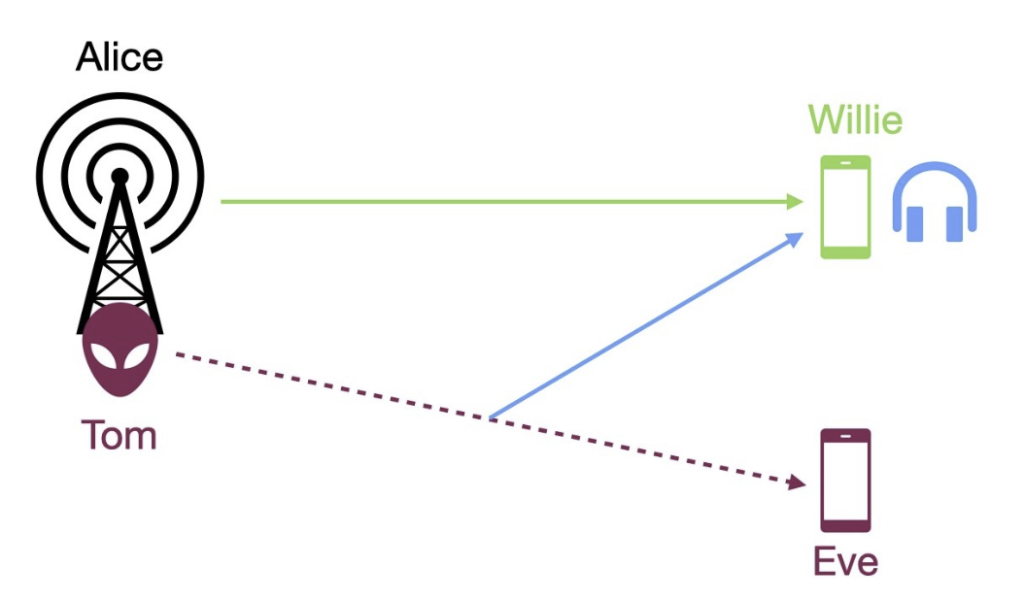
Fig 1: System model of covert communication of a hardware Trojan Tom embedded in a legitimate transmitter Alice trying to communicate with rogue receiver while trying to evade detection from legitimate receiver Willie which acts as the warden.
This project considers covertness in both channel estimation phase and data communication phase. During channel estimation, we adopt a pilot-scaling attack launched by a hardware Trojan. In the communication stage, the Trojan superimposes its signal onto Alice’s transmission. Our results demonstrate that, by exploiting the warden’s nescience of the true channel estimate, the Trojan can transmit covertly to its intended receiver with positive power.
This project addresses several important aspects of covert communication systems including:
- Analytical characterization of the conditions under which covertness can be maintained in both the channel estimation and data transmission phases.
- Demonstration of the simplicity and effectiveness of an adversarial pilot-scaling attack by a hardware Trojan in achieving a positive covert rate.
- Identification of a non-monotonic relationship between the Trojan’s allowable transmit power while remaining covert and the strength of the adversarial attack. (see Fig. 2).
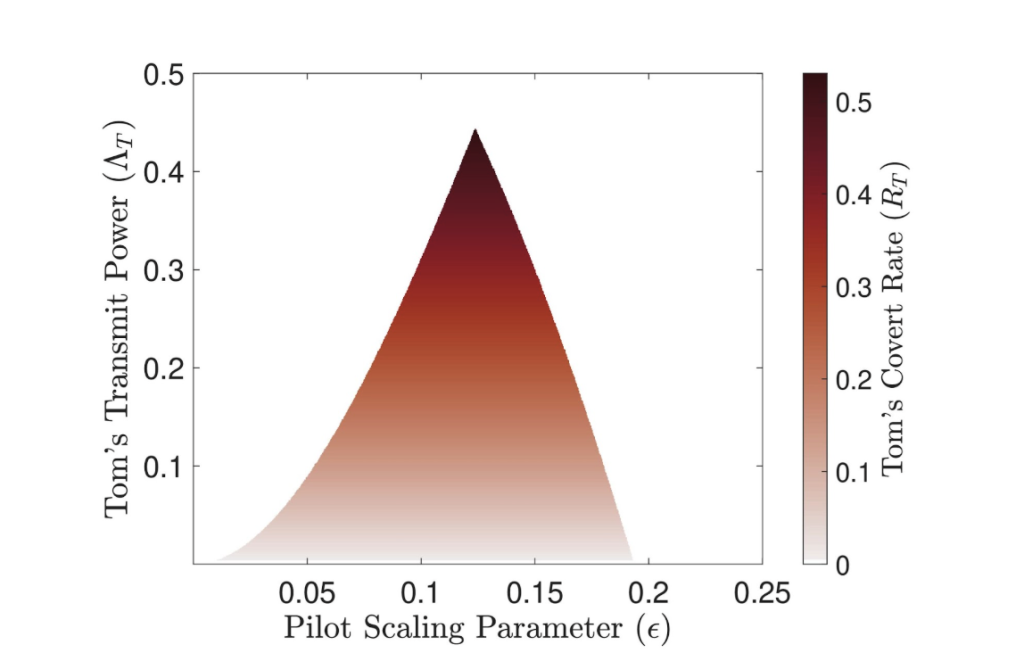
Fig 2: Plot showing the relationship between Tom’s transmit power while staying hidden from Willie and the pilot scaling parameter. After a certain value of pilot-scaling parameter, the increase in self-interference due to incorrect channel estimate causes decoding error in the Alice-Willie communication link which causes decrease in Tom’s transmit power to still ensure covertness.

 2026 Open House
2026 Open House 2025 Brooklyn 6G Summit — November 5-7
2025 Brooklyn 6G Summit — November 5-7 Sundeep Rangan & Team Receive NTIA Award
Sundeep Rangan & Team Receive NTIA Award